When the HTTP protocol was born in 1999, no one ever thought it will be used by one of the most dangerous Cyber threats called Botnet. A bot is an application that can perform and repeat a particular task faster than a human. When a large number of bots infect different targets (e.g. Computers and Mobile Devices) and connect to each other, they form a network of bots or BotNet. A botnets consists of three main elements: the bots, the command and control servers (C&C), and a sophisticated attacker known as a botmaster who designed and control the botnet.
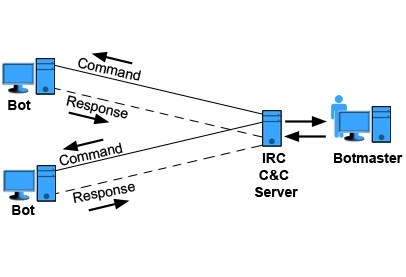
The first generations of botnets use the Internet relay chat or IRC and the relevant channels to establish a central command and control mechanism. The IRC bots follow the PUSH approach as they connect to selected channels and remain in the connect mode. They connect to the IRC servers and channels that have been selected by a botmaster and waits for commands. Although the IRC botnets are easy to use, control and manage, they suffer from a central point of failure.
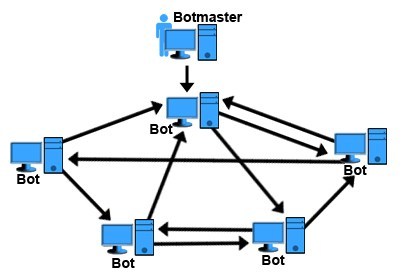
To overcome this issue, the peer to peer architecture is used in the second generation of botnets where instead of having a central C&C server, the botmaster sends a command to one or more bots, and they deliver it to their neighbours.
Since the botmaster commands are distributed by other bots, the botmaster is not able to monitor the delivery status of the commands. Moreover, the implementation of a P2P botnet is difficult and complex. Therefore, botmasters have begun to use the central C&C model again, where the HTTP protocol is used to publish the commands on certain web servers.
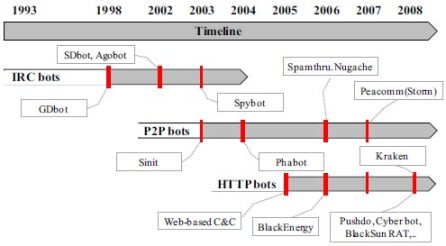
Botnet History by Jae-Seo Lee
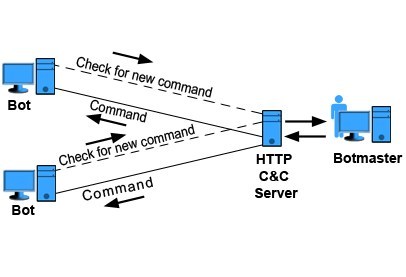
Instead of remaining in connected mode, the HTTP bots periodically visit certain web servers to get updates or new commands. This model is called the PULL style and continues at a regular interval that is defined by the botmaster.
Botmasters use HTTP protocol to hide their activities among the normal web flows and easily avoid current detection methods like firewalls. Therefore, there is no surprise when 6 out of 9 most dangerous Botnets of 2012, were HTTP Botnets.
|
Name |
Description |
| Festi | The Festi, which is also known as a king of spam is one of the most powerful spam and DDoS attackers since 2009. |
| Grum | By having more than 840,000 infected targets all around the world the Grum know as second largest spam botnet in the world. |
| Zeus | The Zeus is one of the most dangerous HTTP-based botnet, which is mainly designed to steal banking information. |
| SpyEye | Like Zeus, the SpyEye is also designed to steal sensitive information. |
| Citadel | It is developed after the Zeus source code to fix the Zeus bugs and shortcomings. |
| TDL-4 | It is a complex http based which uses domain flux technique to periodically change the command and control server domains and avoid detections methods |
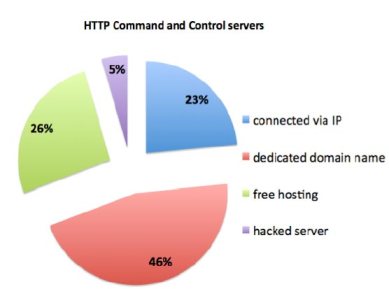
Because of the wide range of HTTP services used, unlike the IRC and P2P, it is not easy to block this service. Moreover, this service is commonly used by normal applications and services in the Internet. some normal applications and services such as Gmail session (which periodically checks for new emails), auto updaters, HTTP based download managers, self-refresh pages and some browsers’ toolbars can generate the same periodic pattern and increase false positive rates in the detection results. Thus, detection of the HTTP botnets with low rate of false alarms (e.g. false negative and false positive) has become a notable challenge. The detection of HTTP Botnets gets even worse where the Botmasters use the legitimate websites (e.g. hacked servers) or normal services (e.g. social bots) to establish their command and controls.
The review of the characteristics of different types of botnets shows that HTTP-based botnets have a set of attributes that make it difficult for them to be detected. On the other hand, the number of studies focusing on the detection of HTTP-based botnets is relatively low (compared to the number of those on IRC-based and P2P botnets) especially in the HTTP-based mobile botnets which operate on the mobile devices and networks.
A POC HTTP Botnet designed to replicate a full weaponised commercial botnet is available at the following URL
https://github.com/Souhardya/UBoat
Meisam Eslahi is an information security researcher and digital forensic investigator, received his Masters’ of Computer Science in Network Security filed. He is working toward the Ph.D. degree in Computer Engineering at UiTM, Malaysia and his domain of interests include Cybersecurity Threats Detection, Mitigation and Response (Mobile Botnets in Particular), Behavioral Analysis, Cybersafety and Digital Awareness. He has over 11 years of experience in the field of Information Technology with 5 being focused on Cyber Security related domains and holds multiple certifications such as CEH (Certified Ethical Hacking), CHFI (Computer Hacking Forensic Investigator), and IBM certified Solution Advisor for Cloud Computing.
[출처] https://securityaffairs.co/wordpress/13747/cyber-crime/http-botnets.html